Fedramp System Security Plan
Fedramp system security plan. Updated Document May 18 2021. The cost-effective security and privacy of other than national security-related information in federal information systems. FedRAMP System Security Plan SSP Moderate Baseline Template.
Switch to PlanStreet and automate your client engagement cases forms and files. If a service is not currently listed as in scope of the most recent assessment it does not mean that you cannot use the service. This System Security Plan provides an overview of the security requirements for the Information System Name Enter Information System Abbreviation and describes the controls in place or planned for implementation to provide a level of security appropriate for the information to be transmitted processed or stored by the system.
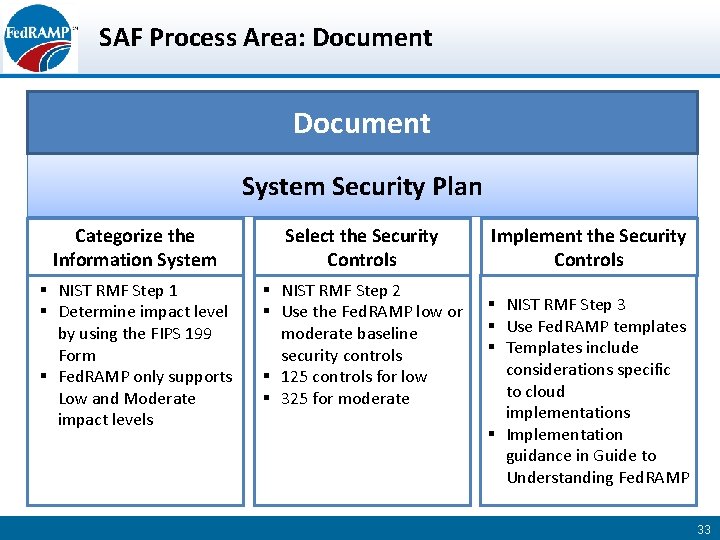
FedRAMP System Security Plan SSP High Baseline Template. This is done through a Security Assessment Plan SAP performing initial and periodic assessments of security controls and producing a Security Assessment Report SAR. For more information on FedRAMP designations see Marketplace Designations for CSPs PDF - 652KB.
Updated Document May 18 2021. We highly recommend engaging with a qualified cybersecurity practitioner to create your system security plan and perform self assessments. Select Azure Government FedRAMP documentation including System Security Plan SSP continuous monitoring reports Plan of Action and Milestones POAM etc is available to customers under NDA and pending access authorization from the Service Trust Portal Audit Reports -.
DevResults is FedRAMP authorized. Updated Document May 18 2021. In our opinion only senior level IT professionals or intermediate level cybersecurity practitioners have the background necessary to fully understand the requirements in 800-171 and CMMC Level 3.
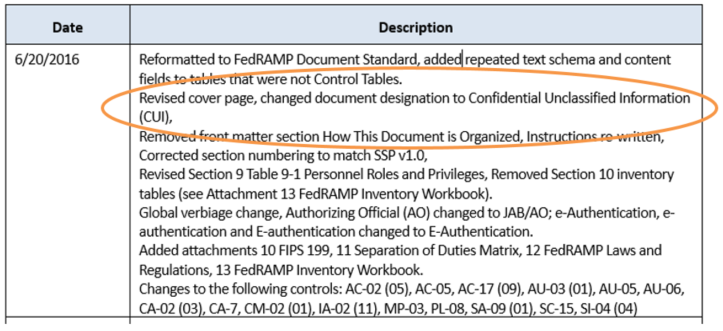
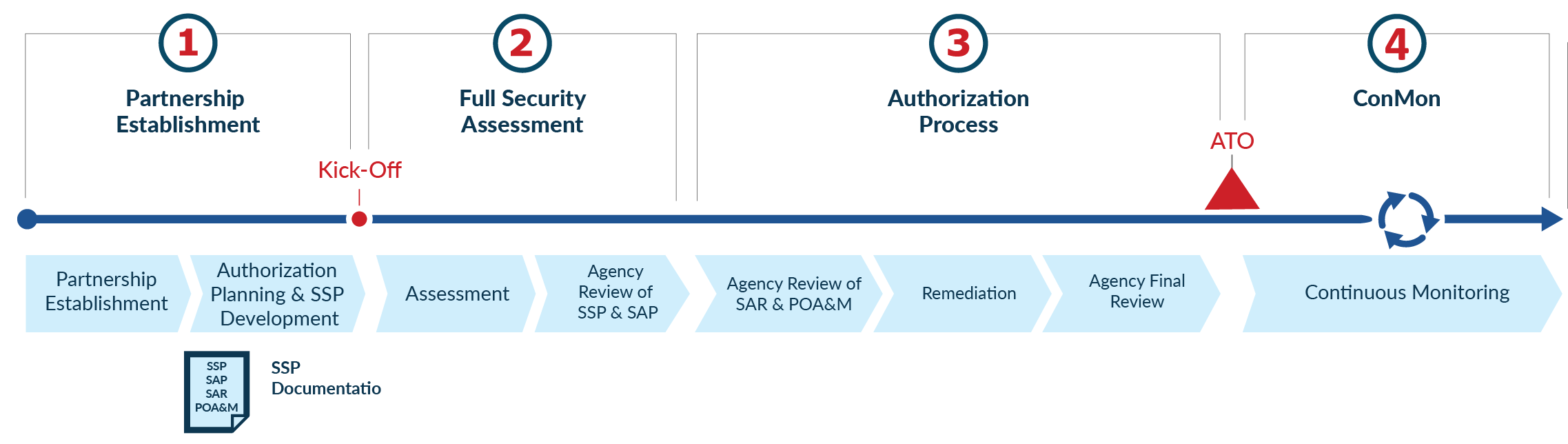
The assessment organization submits a Security Assessment report. We specialize in compliance across multiple industries computer incident response enterprise risk management and more. This is a living document that is meant to be updated as conditions change.
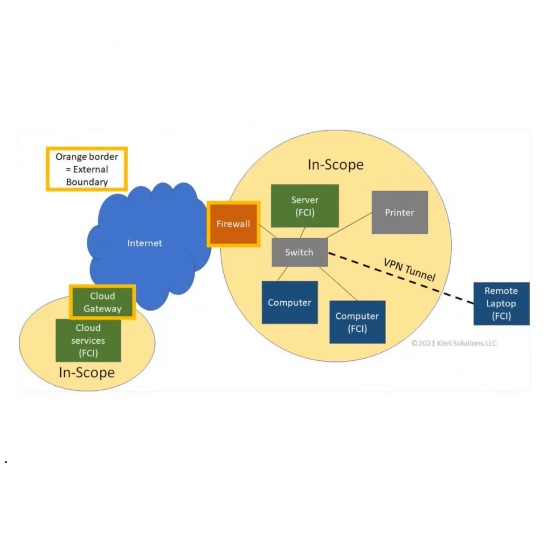
Describes FedRAMP requirements for continuous monitoring incident response and the authorization boundary. After all new security measures and policies do nothing if employees working with the data are not educated on how to minimize risk.
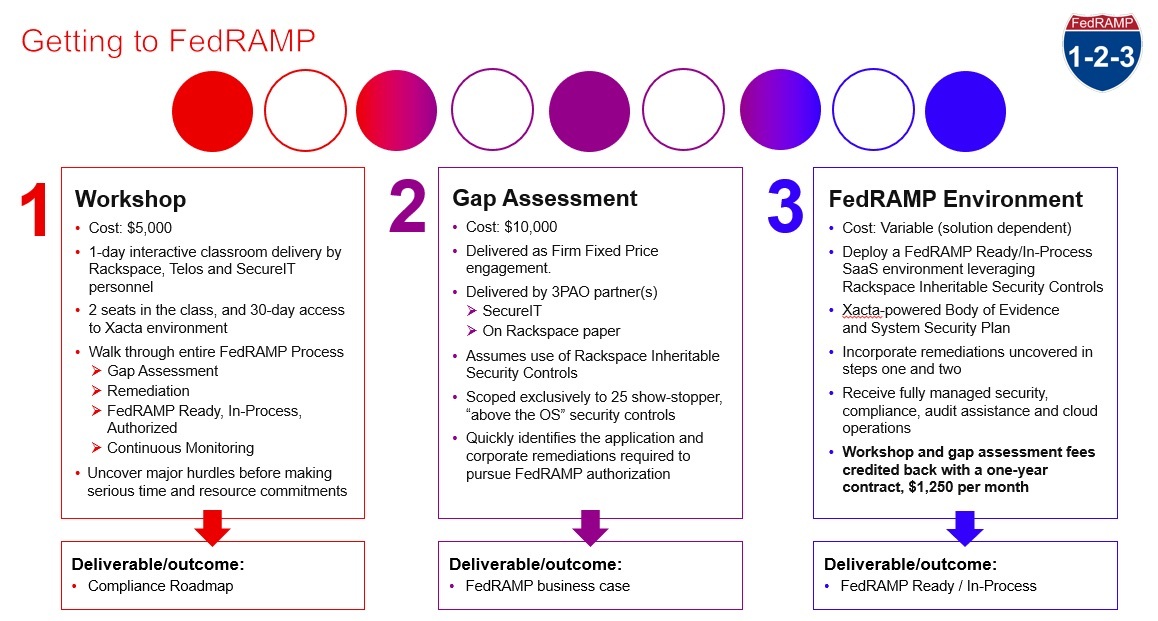
Explain FedRAMP and associated roles and responsibilities.
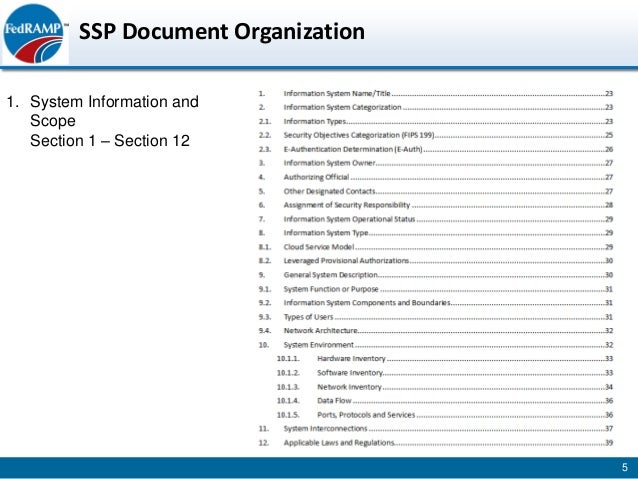
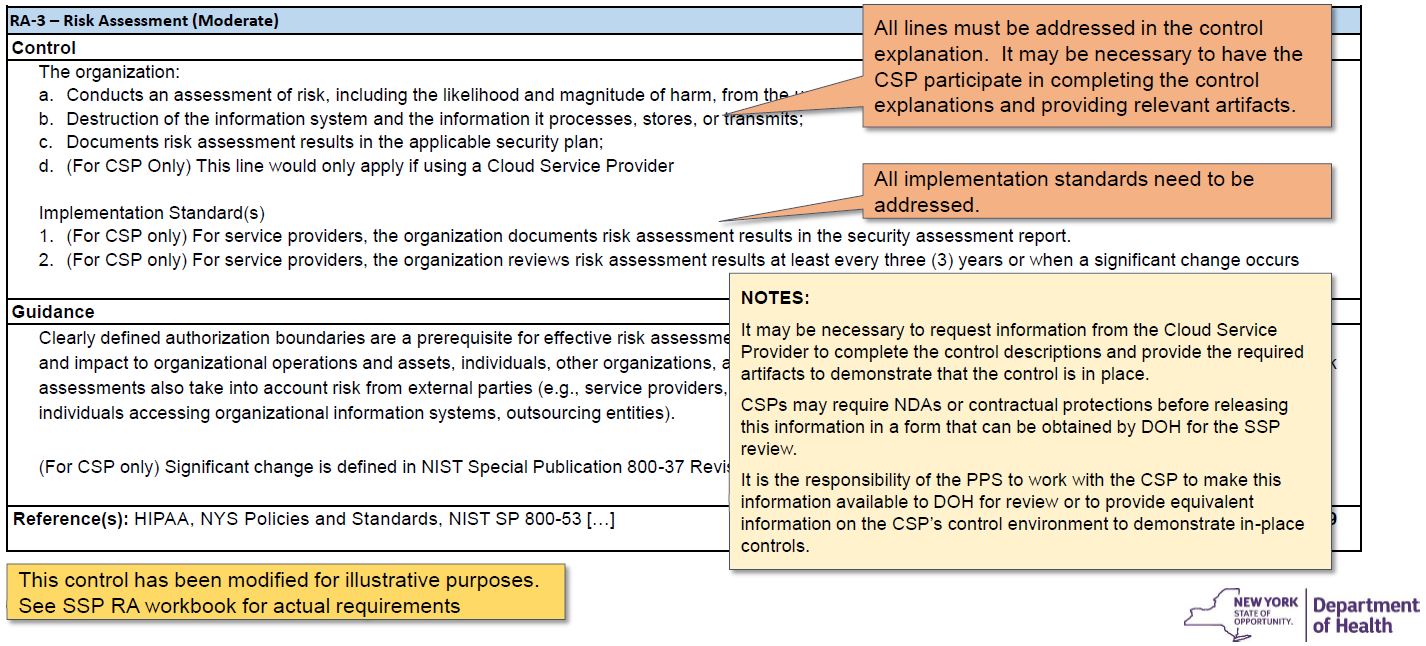
3101 Describing Information System Components 92 SSP. 31 Cloud Service Models Overview. FedRAMP System Security Plan SSP Moderate Baseline Template. 3101 Describing Information System Components 92 SSP. Conduct frequent security awareness trainings to share your information security plan and how each employee plays a role in it. Describes FedRAMP requirements for continuous monitoring incident response and the authorization boundary. The provider creates a Plan of Action Milestones. Program FedRAMP is a government-wide program that provides a standardized approach to. Explain FedRAMP and associated roles and responsibilities.
After all new security measures and policies do nothing if employees working with the data are not educated on how to minimize risk. The following mappings are to the FedRAMP High. Conduct frequent security awareness trainings to share your information security plan and how each employee plays a role in it. DevResults implements industry best practices to ensure the confidentiality and security of client data. We highly recommend engaging with a qualified cybersecurity practitioner to create your system security plan and perform self assessments. If a service is not currently listed as in scope of the most recent assessment it does not mean that you cannot use the service. This is done through a Security Assessment Plan SAP performing initial and periodic assessments of security controls and producing a Security Assessment Report SAR.























-Training_FRblog.png)









Post a Comment for "Fedramp System Security Plan"